パンドラの箱が開けない。

Nessusインストールメモ
Nessusをインストールしてみました。最初は1コアcpu、1Gメモリ、8G HDDの仮想マシンで試したんですが、プラグインインストールの最後の段階で仮想マシンが死んでしまい、どうしてもインストールがうまく行かなかった。それで、サーバーのスペックをアップして、2コアcpu、2Gメモリ、30G HDDの仮想マシンで試したところ無事インストールができました。
# ### http://www.nessus.org からNessus Home バージョンをダウンロードする # ### Activation Codeが必要ですが、上記URLでメールアドレスを入力して申請すれば簡単に取得できる # ls -l /tmp/Nessus-6.3.7-es6.x86_64.rpm -rw-r--r--. 1 xxxxxx xxxxxx 17849819 6月 5 06:06 2015 /tmp/Nessus-6.3.7-es6.x86_64.rpm # rpm -ihv Nessus-6.3.7-es6.x86_64.rpm 警告: Nessus-6.3.7-es6.x86_64.rpm: ヘッダ V4 RSA/SHA1 Signature, key ID 1c0c4a5d: NOKEY 準備中... ########################################### [100%] 1:Nessus ########################################### [100%] Unpacking Nessus Core Components... nessusd (Nessus) 6.3.7 [build M20026] for Linux Copyright (C) 1998 - 2015 Tenable Network Security, Inc Processing the Nessus plugins... [##################################################] All plugins loaded (1sec) - You can start nessusd by typing /sbin/service nessusd start - Then go to https://lpic303-CentOS6:8834/ to configure your scanner # ### サービス起動 # /etc/init.d/nessusd start Nessus サービスを起動中: [ OK ] # ### これでインストール完了
ブラウザーからhttps://ipaddress:8834でアクセス
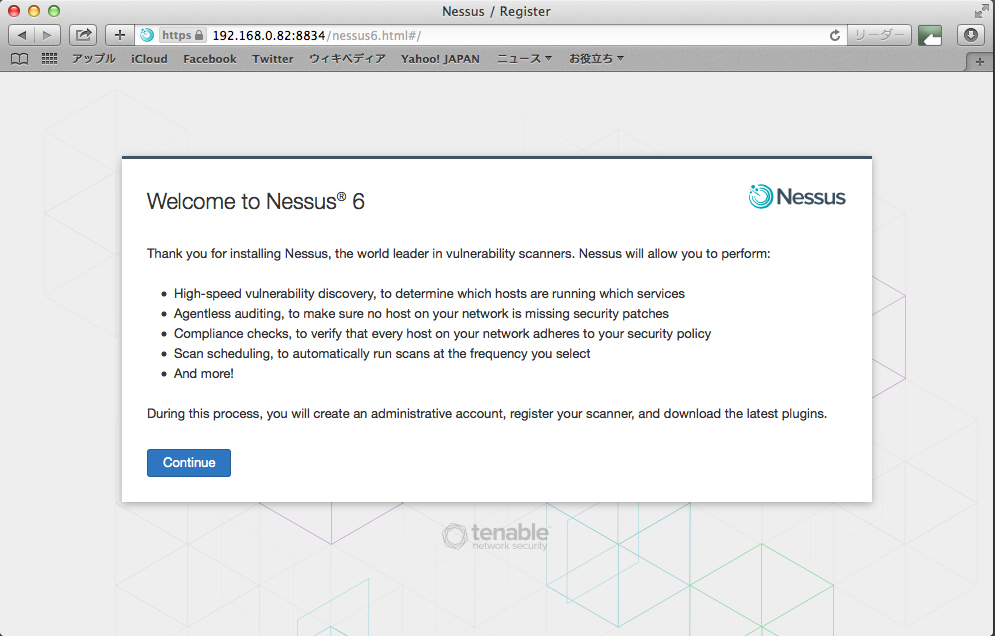
管理用ユーザを作成
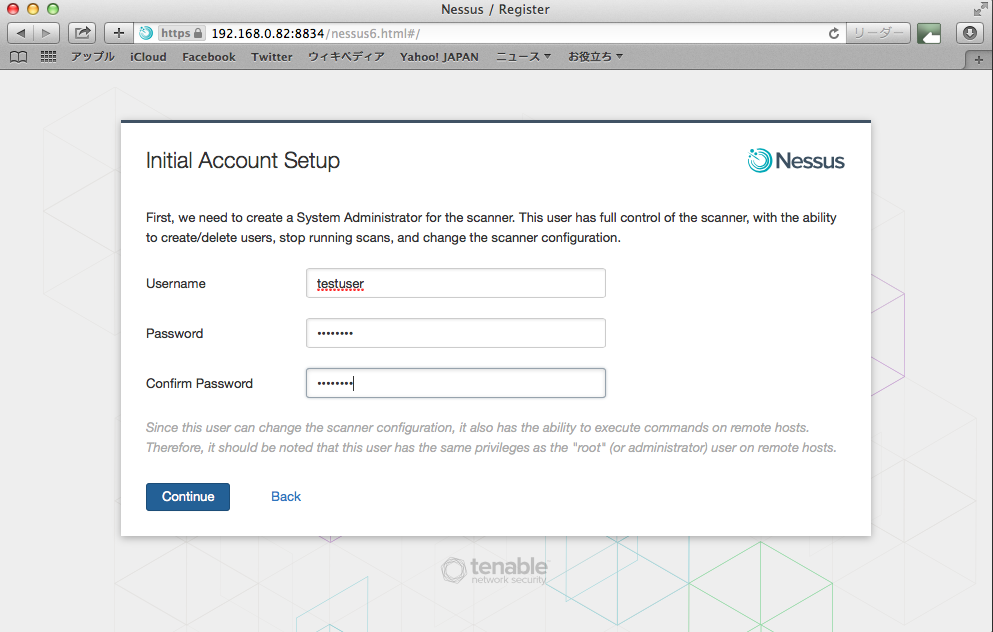
メールで届いたActivation Codeを入力
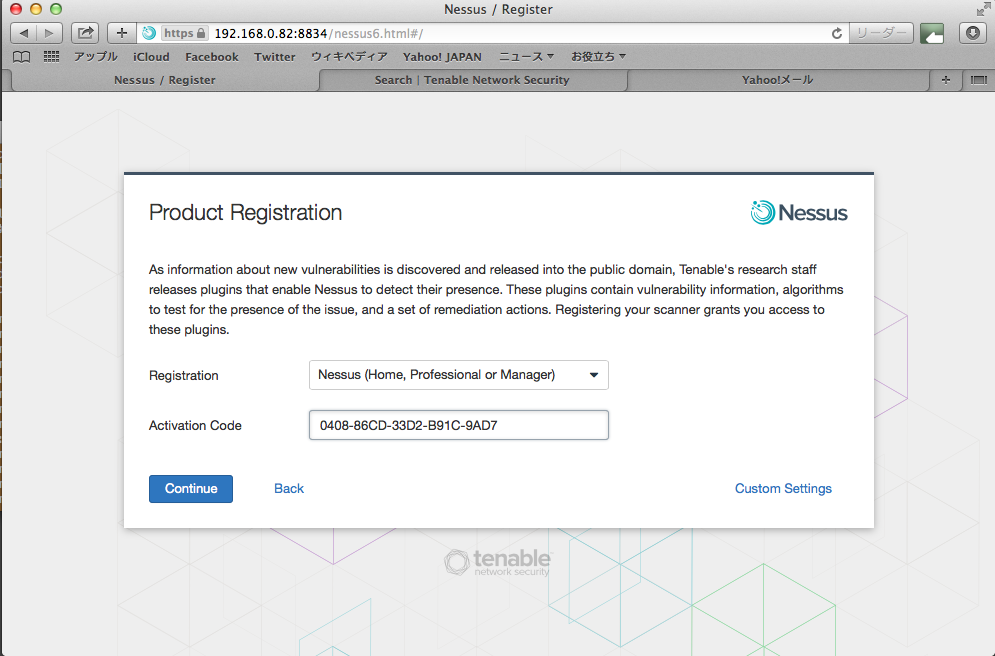
プラグインなどのインストールが始まる、ここは結構時間かかりました。(>40m)

作成したユーザでログイン

新しいポリシーを作成
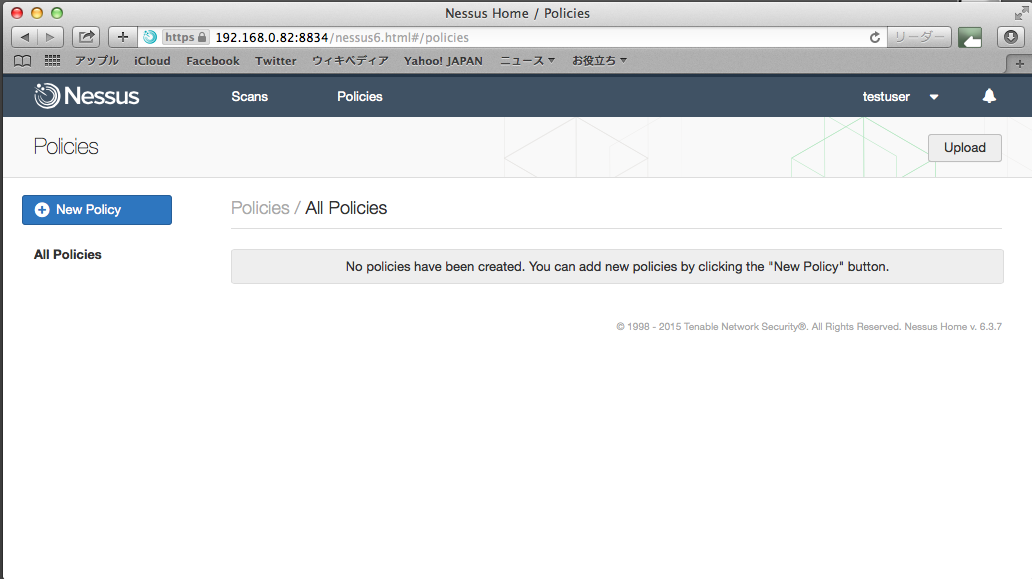
Basic Network Scanを選択
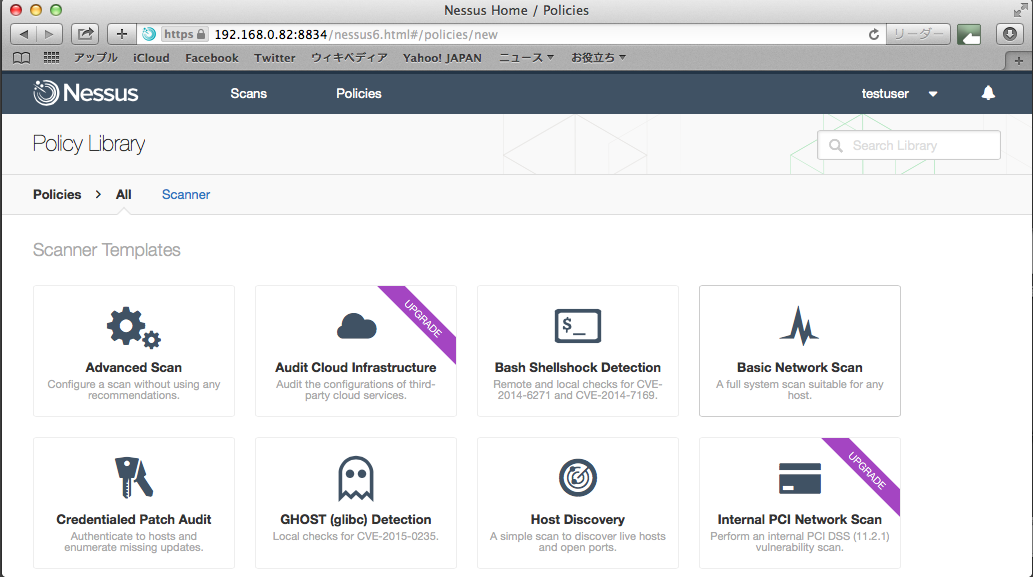
適当なポリシー名前を入れて、保存。その他の項目は全部デフォルト
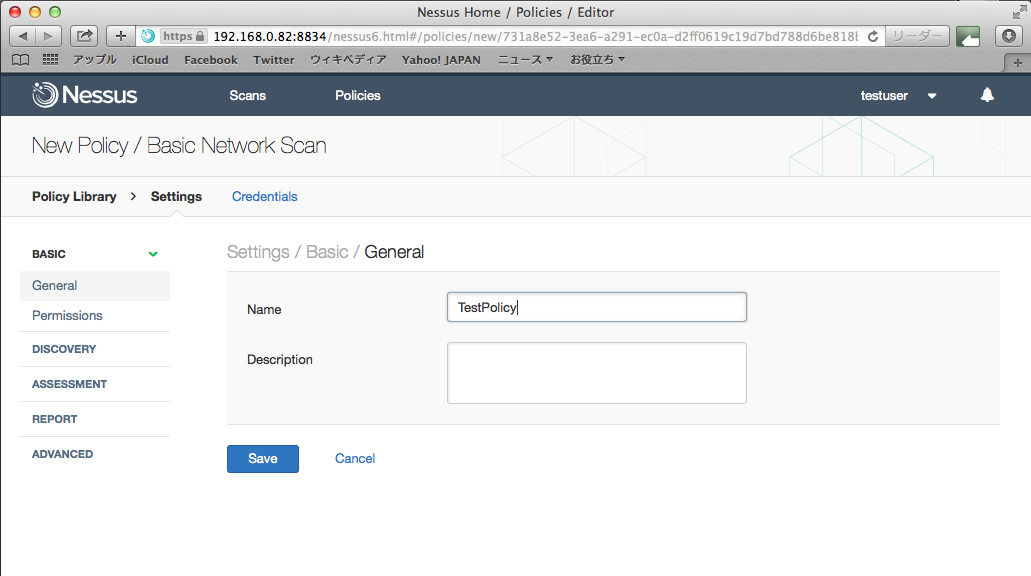
新しいスキャンを作成し、ターゲットのIPアドレスを入力し、スキャン開始
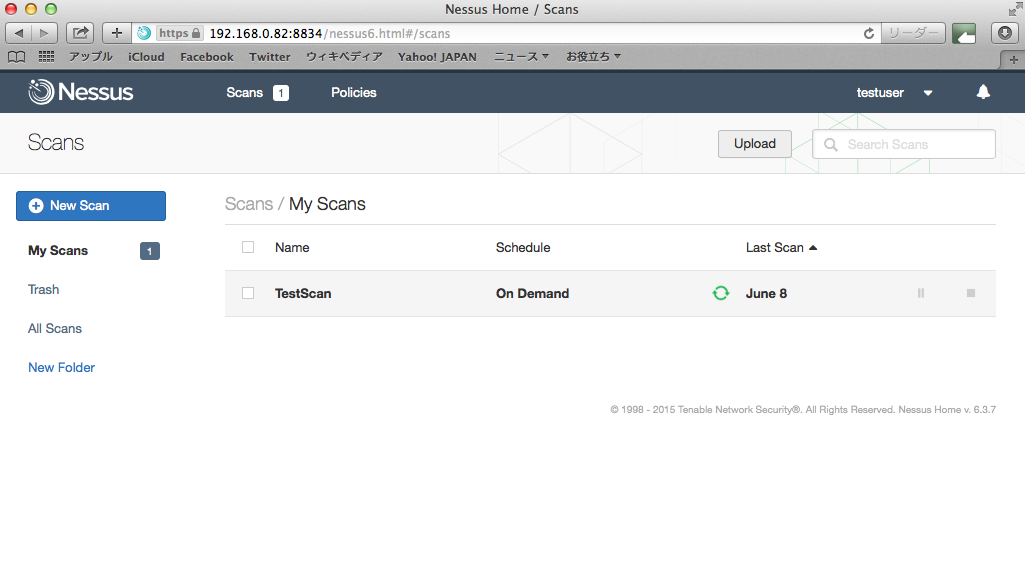
スキャン完了、レコードをクリックすると詳細情報が表示される
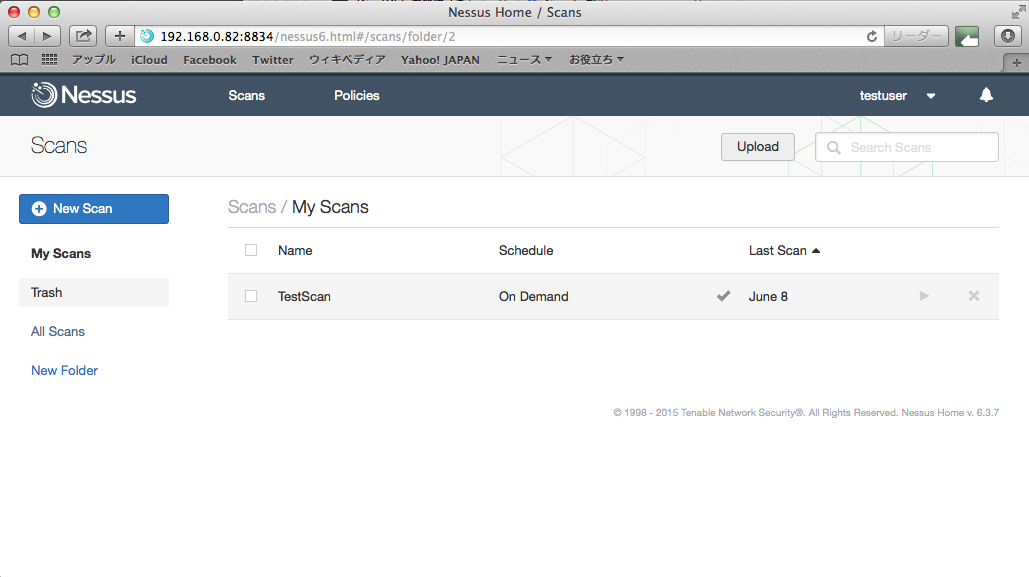
クリックするとさらに詳細情報が表示される
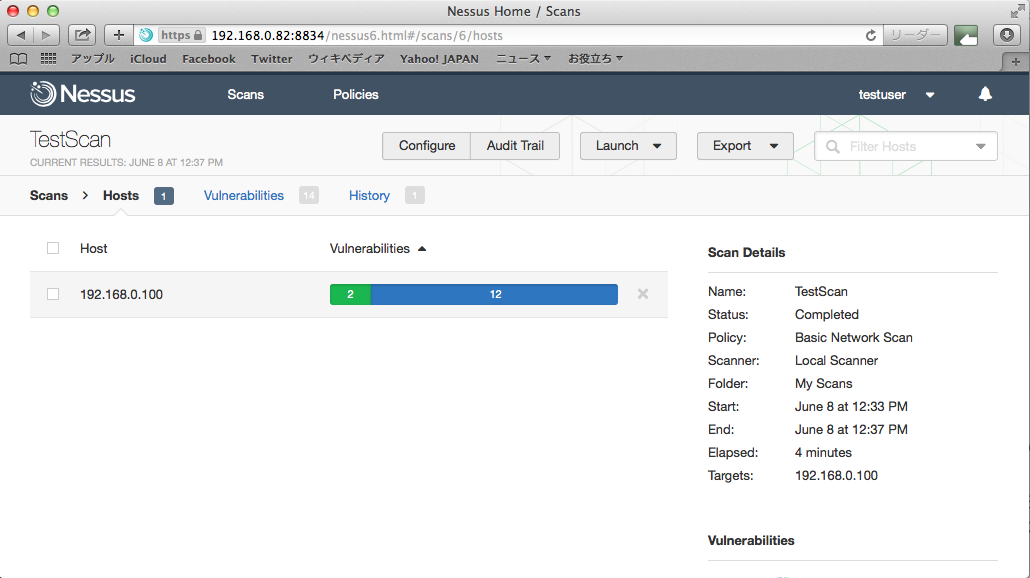
クリックするとさらに詳細情報が表示される
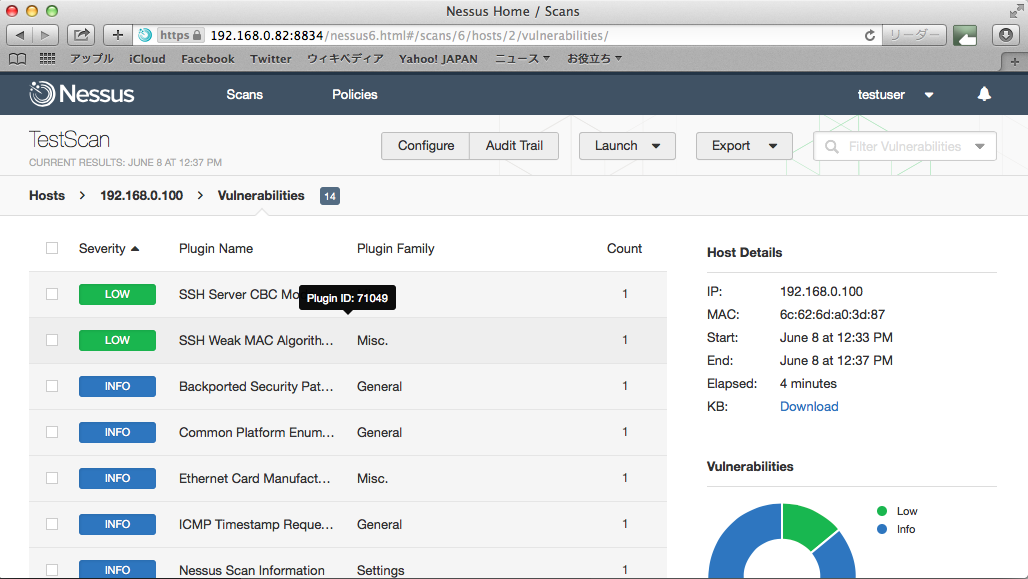
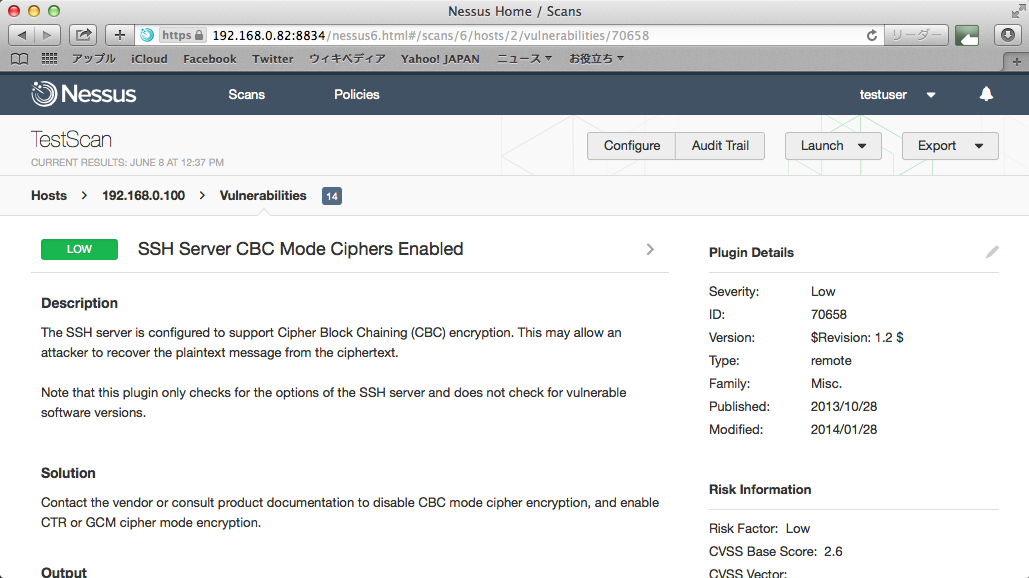
詳細情報
ApacheのDoS対策(勉強メモ)
# ### 1.必要モジュールのインストール
# yum install httpd-devel
# ### 2. ソースを取得、インストール
# cd /tmp/
# wget http://www.zdziarski.com/blog/wp-content/uploads/2010/02/mod_evasive_1.10.1.tar.gz
# tar xvzf mod_evasive_1.10.1.tar.gz
# cd mod_evasive
# apxs -cia mod_evasive20.c
# ### 3. モジュールがインストールされているのを確認
# ls -l /usr/lib64/httpd/modules/ | grep evasive20
-rwxr-xr-x. 1 root root 51149 Jun 5 04:29 mod_evasive20.so
# ### 4.設定ファイルを作成
# vi /etc/httpd/conf.d/mod_evasive20.conf
<IfModule mod_evasive20.c>
DOSHashTableSize 3097
DOSPageCount 2
DOSSiteCount 50
DOSPageInterval 1
DOSSiteInterval 1
DOSBlockingPeriod 10
</IfModule>
# ### 5.Apache再起動
# /etc/init.d/httpd restart
# ### 6. 確認(※)
# perl test.pl
1--------HTTP/1.1 200 OK
2--------HTTP/1.1 200 OK
3--------HTTP/1.1 200 OK
4--------HTTP/1.1 200 OK
5--------HTTP/1.1 200 OK
6--------HTTP/1.1 200 OK
7--------HTTP/1.1 200 OK
8--------HTTP/1.1 200 OK
9--------HTTP/1.1 200 OK
10--------HTTP/1.1 200 OK
11--------HTTP/1.1 200 OK
12--------HTTP/1.1 200 OK
13--------HTTP/1.1 200 OK
14--------HTTP/1.1 200 OK
15--------HTTP/1.1 200 OK
16--------HTTP/1.1 200 OK
17--------HTTP/1.1 403 Forbidden
18--------HTTP/1.1 403 Forbidden
19--------HTTP/1.1 403 Forbidden
・・・
98--------HTTP/1.1 403 Forbidden
99--------HTTP/1.1 403 Forbidden
100--------HTTP/1.1 403 Forbidden
101--------HTTP/1.1 403 Forbidden
### テスト用スクリプトをちょっとだけ修正しています
root@lpic303-CentOS6 mod_evasive]# cat test.pl
#!/usr/bin/perl
# test.pl: small script to test mod_dosevasive's effectiveness
use IO::Socket;
use strict;
my $count = 1;
for(0..100) {
my($response);
my($SOCKET) = new IO::Socket::INET( Proto => "tcp",
PeerAddr=> "127.0.0.1:80");
if (! defined $SOCKET) { die $!; }
print $SOCKET "GET /?$_ HTTP/1.0\n\n";
$response = <$SOCKET>;
print $count++;
print "--------";
print $response;
close($SOCKET);
}
| DOSPageIntervalDOSPageCount | DOSPageIntervalで設定した秒数以内で、同じページにアクセスできる上限数 |
| DOSBlockingPeriod | ブラックリストへ登録された接続元を遮断する時間(ミリ秒) |
Tripwire導入メモ
### 1.ソースの取得とインストール
# cd /usr/local/src/
# wget http://jaist.dl.sourceforge.net/project/tripwire/tripwire-src/tripwire-2.4.2.2/tripwire-2.4.2.2-src.tar.bz2
# tar jxvf tripwire-2.4.2.2-src.tar.bz2
# cd tripwire-2.4.2.2-src
# ./configure
# make
# make install
### 2.テスト用の監視対象ファイルを作成
# touch /tmp/sample.txt
### 3.動作確認のためのポリシーファイル作成
vi /tmp/twpol.txt
(
rulename = "Sample", )
{
/tmp/sample.txt -> +p;
}
# twadmin --create-polfile --site-keyfile /usr/local/etc/site.key /tmp/twpol.txt
### 4.データベースを初期化
# tripwire --init
### 5.なんの変更もない状態で確認
# tripwire --check
Parsing policy file: /usr/local/etc/tw.pol
*** Processing Unix File System ***
Performing integrity check...
Wrote report file: /usr/local/lib/tripwire/report/lpic303-CentOS6-20150605-035915.twr
Open Source Tripwire(R) 2.4.2.2 Integrity Check Report
Report generated by: root
Report created on: Fri Jun 5 03:59:15 2015
Database last updated on: Fri Jun 5 03:39:02 2015
===============================================================================
Report Summary:
===============================================================================
Host name: lpic303-CentOS6
Host IP address: Unknown IP
Host ID: None
Policy file used: /usr/local/etc/tw.pol
Configuration file used: /usr/local/etc/tw.cfg
Database file used: /usr/local/lib/tripwire/lpic303-CentOS6.twd
Command line used: tripwire --check
===============================================================================
Rule Summary:
===============================================================================
-------------------------------------------------------------------------------
Section: Unix File System
-------------------------------------------------------------------------------
Rule Name Severity Level Added Removed Modified
--------- -------------- ----- ------- --------
Sample 0 0 0 0
(/tmp/sample.txt)
Total objects scanned: 1
Total violations found: 0
===============================================================================
Object Summary:
===============================================================================
-------------------------------------------------------------------------------
# Section: Unix File System
-------------------------------------------------------------------------------
No violations.
===============================================================================
Error Report:
===============================================================================
No Errors
-------------------------------------------------------------------------------
*** End of report ***
Open Source Tripwire 2.4 Portions copyright 2000 Tripwire, Inc. Tripwire is a registered
trademark of Tripwire, Inc. This software comes with ABSOLUTELY NO WARRANTY;
for details use --version. This is free software which may be redistributed
or modified only under certain conditions; see COPYING for details.
All rights reserved.
Integrity check complete.
### 6. 変更を加える
setfacl -m user:testuser:rwx /tmp/sample.txt
### 7. 再度チェック
tripwire --check
Parsing policy file: /usr/local/etc/tw.pol
*** Processing Unix File System ***
Performing integrity check...
Wrote report file: /usr/local/lib/tripwire/report/lpic303-CentOS6-20150605-040008.twr
Open Source Tripwire(R) 2.4.2.2 Integrity Check Report
Report generated by: root
Report created on: Fri Jun 5 04:00:08 2015
Database last updated on: Fri Jun 5 03:39:02 2015
===============================================================================
Report Summary:
===============================================================================
Host name: lpic303-CentOS6
Host IP address: Unknown IP
Host ID: None
Policy file used: /usr/local/etc/tw.pol
Configuration file used: /usr/local/etc/tw.cfg
Database file used: /usr/local/lib/tripwire/lpic303-CentOS6.twd
Command line used: tripwire --check
===============================================================================
Rule Summary:
===============================================================================
-------------------------------------------------------------------------------
Section: Unix File System
-------------------------------------------------------------------------------
Rule Name Severity Level Added Removed Modified
--------- -------------- ----- ------- --------
* Sample 0 0 0 1
(/tmp/sample.txt)
Total objects scanned: 1
Total violations found: 1
===============================================================================
Object Summary:
===============================================================================
-------------------------------------------------------------------------------
# Section: Unix File System
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
Rule Name: Sample (/tmp/sample.txt)
Severity Level: 0
-------------------------------------------------------------------------------
Modified:
"/tmp/sample.txt"
===============================================================================
Error Report:
===============================================================================
No Errors
-------------------------------------------------------------------------------
*** End of report ***
Open Source Tripwire 2.4 Portions copyright 2000 Tripwire, Inc. Tripwire is a registered
trademark of Tripwire, Inc. This software comes with ABSOLUTELY NO WARRANTY;
for details use --version. This is free software which may be redistributed
or modified only under certain conditions; see COPYING for details.
All rights reserved.
Integrity check complete.
### 8. レポート確認
# twprint --print-report --report-level 0 --twrfile /usr/local/lib/tripwire/report/lpic303-CentOS6-20150605-040008.twr
Note: Report is not encrypted.
TWReport lpic303-CentOS6 20150605040008 V:1 S:0 A:0 R:0 C:1
————————————————
V:違反の数
S:重要度
A:追加されたファイル・ディレクトリ
R:削除されたファイル・ディレクトリ
C:変更されたファイル・ディレクトリ
————————————————
### 9.データベースの更新
# tripwire --update --twrfile /usr/local/lib/tripwire/report/lpic303-CentOS6-20150605-040008.twr
Please enter your local passphrase:
Wrote database file: /usr/local/lib/tripwire/lpic303-CentOS6.twd
### 10.システム設定ファイルの内容表示・編集
# twadmin --print-cfgfile
ROOT =/usr/local/sbin
POLFILE =/usr/local/etc/tw.pol
DBFILE =/usr/local/lib/tripwire/$(HOSTNAME).twd
REPORTFILE =/usr/local/lib/tripwire/report/$(HOSTNAME)-$(DATE).twr
SITEKEYFILE =/usr/local/etc/site.key
LOCALKEYFILE =/usr/local/etc/lpic303-CentOS6-local.key
EDITOR =/bin/vi
LATEPROMPTING =false
LOOSEDIRECTORYCHECKING =false
MAILNOVIOLATIONS =true
EMAILREPORTLEVEL =3
REPORTLEVEL =3
MAILMETHOD =SENDMAIL
SYSLOGREPORTING =false
MAILPROGRAM =/usr/sbin/sendmail -oi -t
### 11.ポリシーファイルの内容確認
# twadmin --print-polfile
(
rulename = "Sample", )
{
/tmp/sample.txt -> +p;
}
WebサーバーのSSL設定
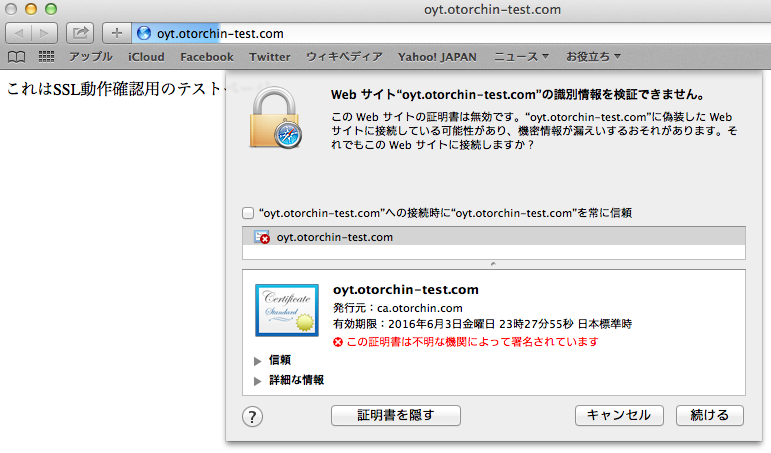
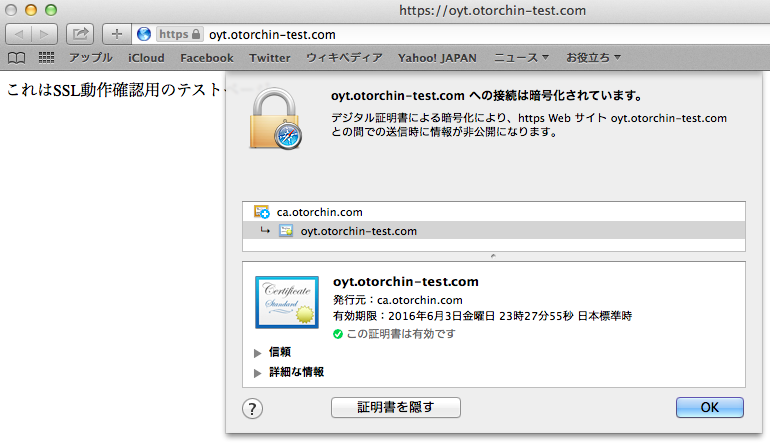
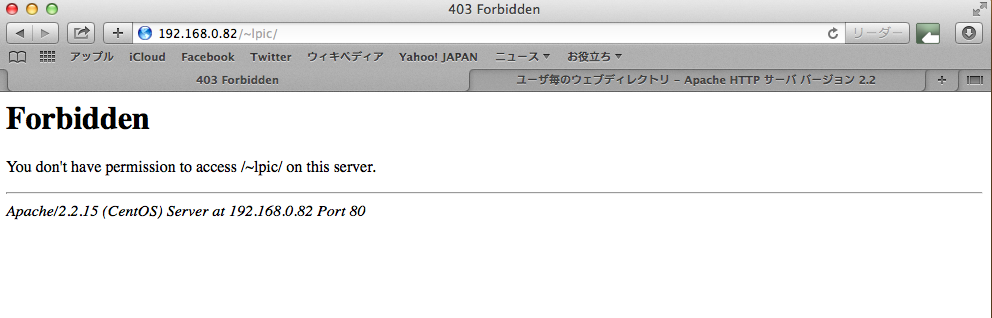
WebサーバーのSSL設定について、勉強したメモ。OSはCentOS6.4。簡易手順ですが、
| 1.サーバーの秘密鍵を作成 | |
| 2.CSRの作成 | |
| 3.自分でCAを構築 | |
| 4.CSRをCAに送る | |
| 5.サイト証明書を発行 | |
| 6.Apacheの設定、再起動 | |
| 7.確認 |